As the CEO of FullProxy, I’ve always believed that staying ahead of technological disruptions is increasingly the most pressing concern for businesses and public sector organisations across the globe – not just from a cyber security perspective, but as a fundamental safeguard against business interruption.
Recently, I attended our joint presentation with AppViewX, “Certificate Lifecycles Matter: Turning Google’s 90 Day Rule into a Security Advantage,” at DIGIT Expo in Edinburgh, where a critical message from our expert speaker resonated with me deeply; our approach to cryptography is about to undergo a fundamental transformation.
The Quantum Computing Sword of Damocles
We’re standing at the precipice of a technological revolution. Quantum computing isn’t just another incremental tech advancement. It’s a potential skeleton key that could unlock encrypted data we’ve long considered secure.
Today’s asymmetric cryptographic algorithms, which we’ve relied on for encryption and digital signatures, are increasingly vulnerable. As quantum computing capabilities advance, what was once thought unbreakable now looks remarkably fragile. This isn’t a distant, theoretical concern; it’s an imminent challenge that demands immediate attention from every security professional.
Beyond Worry: A Proactive Approach to Combatting the post-Quantum Threat
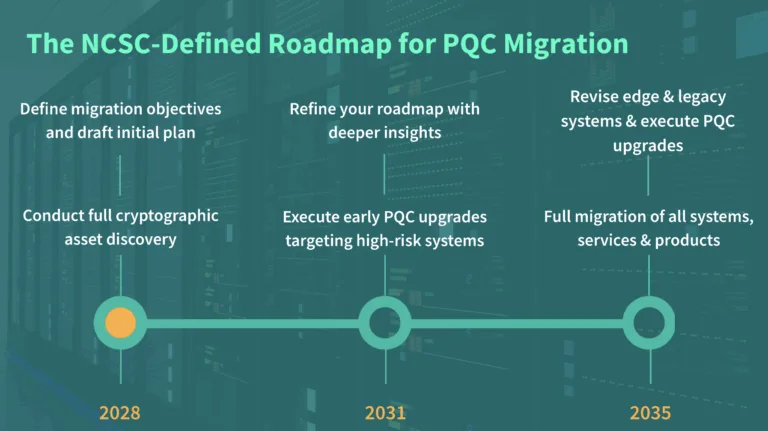
During the presentation, Murali Palanisamy from AppViewX made a point that crystallised our collective challenge; certificate management systems will be essential in a post-quantum world. This isn’t just a technical observation – it’s a strategic one. Businesses must develop a crypto-agile mindset.
This means:
- Continuously updating cryptographic libraries
- Preparing for seamless transitions to quantum-safe algorithms
- Understanding the evolving landscape of cryptographic security
“This isn’t just a technical observation – it’s a strategic one. Businesses must develop a crypto-agile mindset. “
Why Certificate Management is Your Quantum Threat Shield
Certificate lifecycle management is no longer just about compliance or routine maintenance. It’s becoming our primary mechanism for quantum resilience. By implementing robust, adaptable certificate management systems, you can:
- Rapidly integrate new, quantum-resistant cryptographic algorithms
- Minimise disruption during critical security transitions
- Maintain continuous, secure communications in an increasingly complex threat landscape
The tech giants know this is coming; the imminence of quantum is the reason Apple and Google are implementing short lifecycles now. And in our view, the shorter the certificate lifecycle, the better it is for your cyber security. This does mean, however, a change in our approach to cert management, from reactive to strategic.
Read CTO Chris Templeton’s recent article on preparing for shorter certificate lifecycles here.
“The tech giants know this is coming; the imminence of quantum is the reason Apple and Google are implementing short lifecycles now.”
Tech Leaders – I’m Speaking to You
To my fellow technology and security leaders: the quantum threat is real, and a lack of prep could see some serious vulnerabilities crop up in the years to come. We must:
- Invest in crypto-agile infrastructure
- Train our teams to understand quantum computing’s implications
- Partner with forward-thinking technology providers who are already developing quantum-ready solutions
At FullProxy, we’re committed to being at the forefront of this transformation. Our partnership with AppViewX represents more than a business relationship-it’s a shared mission to secure the digital future.
The quantum era is coming. Will you be ready?
Learn how we can help you with your certificate management needs today!