What is the PQC timeline?
In May 2025, the UK’s National Cyber Security Centre (NCSC) released a Post-Quantum Cryptography (PQC) migration timeline. It maps out how your organisation needs to prepare for the coming quantum shift – a near future where today’s seemingly secure encryption could be broken by quantum computers.
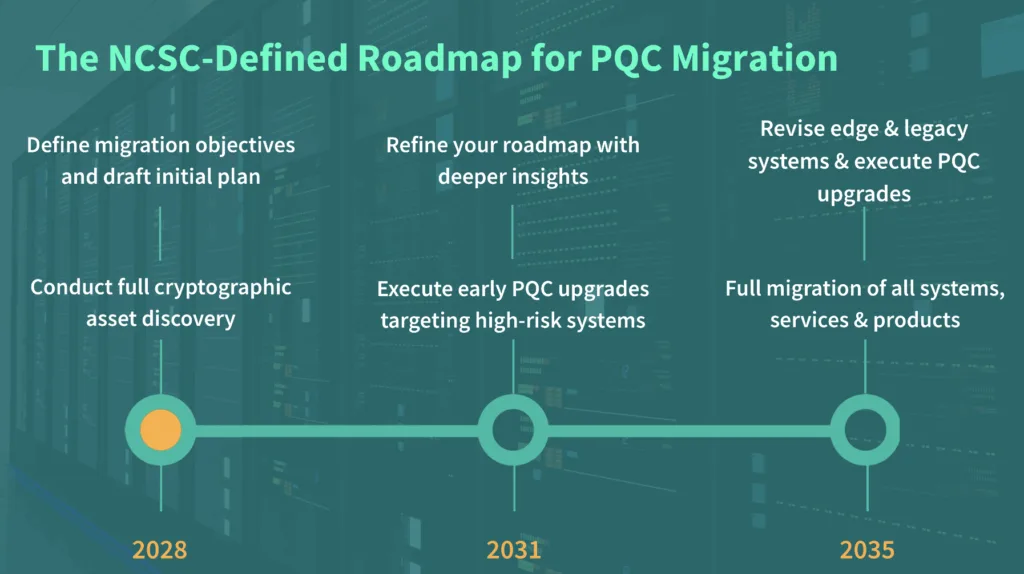
The roadmap sets three key milestones the first target in 2028. In fact the US version of the NCSC – NIST – sets the first action point at 2026. The truth is that we don’t know when PQC will happen, so FullProxy’s advice would be to meet the earliest date you can so you’re not a soft target. Whichever you follow, very soon you need to have:
- A completed cryptographic inventory
- An understanding of where vulnerable algorithms are in use
- Begun planning for a phased migration to PQC-ready infrastructure
Sounds manageable. But if 2028 feels a long way off, here’s why it isn’t:
Why 2028 isn’t really far away
For most enterprises, less than 3 years isn’t much time when it comes to IT transformation:
- Inventory takes longer than you think. Many organisations can’t easily see which encryption standards are in use across certificates, applications and devices.
- Dependencies run deep. Cryptographic libraries touch almost every system; replacing them without breaking business processes requires planning and testing.
- Budgets cycles are slow. Even if you start now, aligning PQC projects with existing IT refresh cycles can take years.
That’s why the NCSC is urging IT and security leaders to begin now, not later.
“We don’t know when PQC will happen, so FullProxy’s advice would be to meet the earliest date you can so you’re not a soft target”
Ewan Ferguson, CEO at FullProxy
The risks of waiting
It’s tempting to put PQC readiness on the “future problems” list. But waiting until 2027 or 2028 creates real risks:
- Crypto debt: the longer outdated encryption persists, the harder and more expensive it is to replace.
- Compliance gaps: regulators are expected to align with the NCSC’s timeline, meaning non-compliance could become a financial and reputational issue.
- Lost agility: organisations without crypto-agility will struggle to adapt quickly once PQC algorithms are standardised.
What should I do first?
The NCSC highlights one crucial first step: know what you’ve got.
- Run a cryptographic inventory scan to map certificates, keys and algorithms in use.
- Identify systems using vulnerable algorithms like RSA and ECC.
- Begin planning for crypto-agility, ensuring your systems can pivot fast when PQC standards are finalised.
How FullProxy can help
FullProxy’s cyber experts work with our leading partners – AppViewX, F5 and Fortinet – to make PQC readiness practical:
- AppViewX AVX ONE automates certificate discovery and lifecycle management.
- F5 BIG-IP centralises visibility over encrypted traffic and PQC defends your perimeter
- Fortinet NGFWs protect performance and enable secure migration without disruption.
Together, these solutions provide visibility, agility and protection — the three pillars of PQC readiness.
Next steps:
Don’t wait for 2028 to come around. Start your PQC journey today:




