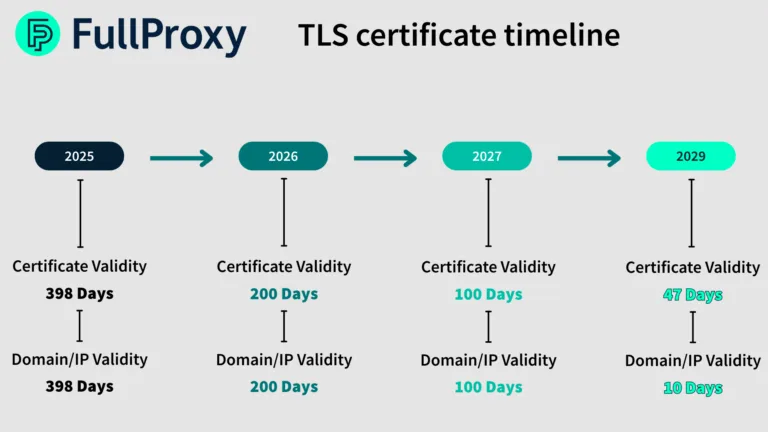
The push for certificate lifecycle reduction stems from a fundamental truth: certificate lifecycle management is not a team member’s core job role – it's often an afterthought and annoyance, a general admin task. With these changes, this will fundamentally not be the case.