Gartner predicts that by 2023, 60% of enterprises will phase out traditional VPNs and use a ZTNA model.
Gartner defines Zero Trust Network Access (ZTNA) as…
“a product or service that creates an identity- and context-based, logical access boundary around an application or set of applications. The applications are hidden from discovery, and access is restricted via a trust broker to a set of named entities. The broker verifies the identity, context and policy adherence of the specified participants before allowing access and prohibits lateral movement elsewhere in the network. This removes application assets from public visibility and significantly reduces the surface area for attack.”
Building a zero-trust network access solution requires a variety of components—a client, a proxy, authentication, and security. But in most organisations, these solutions are provided by different vendors. The components often run on different operating systems and use different consoles for management and configuration, so establishing a zero-trust model across vendors is nearly impossible.
With Fortinet, not only can you easily establish zero-trust access through one vendor but also with one operating system. FortiOS 7.0 updates turn an organisation’s existing Fortinet infrastructure into the newest part of a zero-trust architecture. FortiGate next-generation firewalls (NGFWs) and FortiClient endpoint protection employ ZTNA capabilities with simplified management. The same adaptive, application access policy is used whether users are on or off the network. And, by building ZTNA into FortiOS, it’s tightly integrated into the Fortinet Security Fabric, enabling easy management and superior visibility.
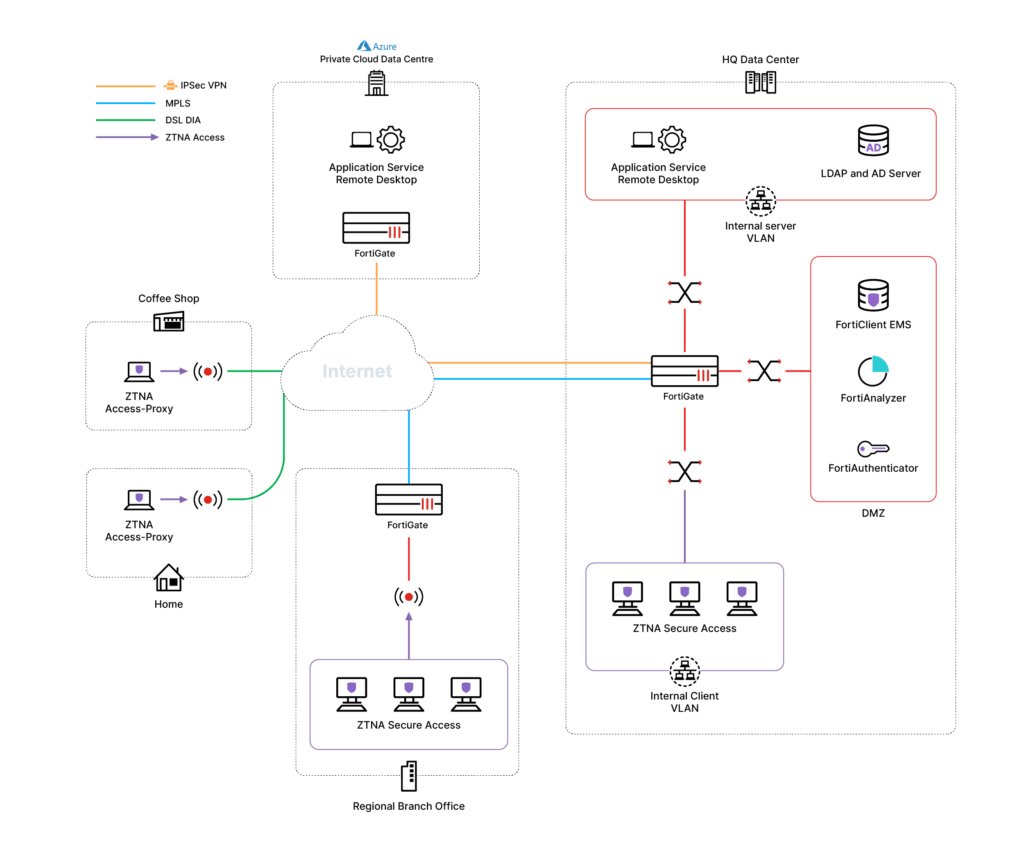
Fortinet can apply ZTNA to remote users, home offices, and other locations, such as retail stores, by offering controlled remote access to applications. It’s easier and faster to initiate than a traditional VPN. This gives users a better experience while providing a more granular set of security protections. It doesn’t matter if applications are in the data centre, private cloud, or public cloud. Users and applications can be geographically independent and still create secure and reliable connections.
Enables ZTNA policies to be enforced for both remote workers and on-campus workers.
Grants access to a specific application only for that session.
Verifies the user identity, the device identity, device posture, and the user’s right to access an application before granting access to an application.
Provides more visibility and control of the endpoint for the IT team while providing the user a faster, easier experience.
Requires no additional licenses. Fortinet’s ZTNA is a free feature in FortiOS and FortiClient, enabling customers to shift from VPN to ZTNA at their own pace.
Creates TLS-encrypted tunnels automatically, from the endpoint to the access proxy, ensuring traffic is hidden from prying eyes.
Endpoint Agent for Visibility and Control, Endpoint Protection, and Secure Remote Access using VPN and Zero Trust Technologies
FortiClient ZTNA works with FortiOS to enable secure granular access to applications no matter if the user is local or remote. Each session is initiated with an automatic, encrypted tunnel from FortiClient to the FortiOS proxy point for user and device verification. If verified, access is granted for that session. You can also use multifactor authentication to provide an additional layer of security. With ZTNA, organizations benefit from both a better remote access solution and a consistent policy for controlled access to applications irrespective of endpoint location.
Trust Broker
FortiGate acts as the Access Proxy which sits between the endpoints and applications, and continuously validates the posture and identity of each connection, and providing secure micro-segmented access for each session. The access proxy is a feature of FortiGate and natively integrated with SDWAN, SASE, NGFW and all other FortiGate components.
User Identity Management and Single Sign-On
FortiAuthenticator is the gatekeeper of authorization into the Fortinet secured enterprise network identifying users, querying access permissions from third party systems, and communicating this information to FortiGate devices for use in Identity-Based Policies. This additional layer of security greatly reduces the possibility of data leaks while helping companies meet audit requirements associated with government and business privacy regulations.
Enable two-factor authentication with FortiToken Mobile (FTM) One-Time Password (OTP) Application with Push Notifications or a Hardware Time-Based OTP Token
Fortinet FortiToken Mobile (FTM) and hardware OTP Tokens are fully integrated with FortiClient, protected by FortiGuard, and leverage direct management and use within the FortiGate and FortiAuthenticator security platforms. Fortinet two-factor authentication solutions are easy to manage and easy to use.







Minimise your security risk.
Maximise your return on investment.